Google's "Smart Lock" and Android Autofill
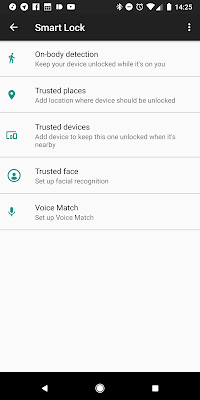
Have you ever heard of Google's " Smart Lock "? When I first discovered Smart Lock, it was just a feature of Android that allowed your device to remain unlocked as long as certain conditions were met - such as being at a specific location (say, at home), the front camera recognizing your face (you mean "Face ID" has been around for a long time? yes, and it never worked well and still doesn't work well, even on iPhone), your phone being on your body, or connected to a trusted device. Recently Google has added another piece of functionality to Smart Lock called Smart Lock for Passwords. I first noticed this inside the Netflix application probably one or two years ago when I was offered to automatically sign in because my login info at the time was saved in my Google Chrome password manager, but no other apps that I used regularly seemed to have this new functionality. Looking at the developer page for this feature, it makes sense as to why since it ap...





